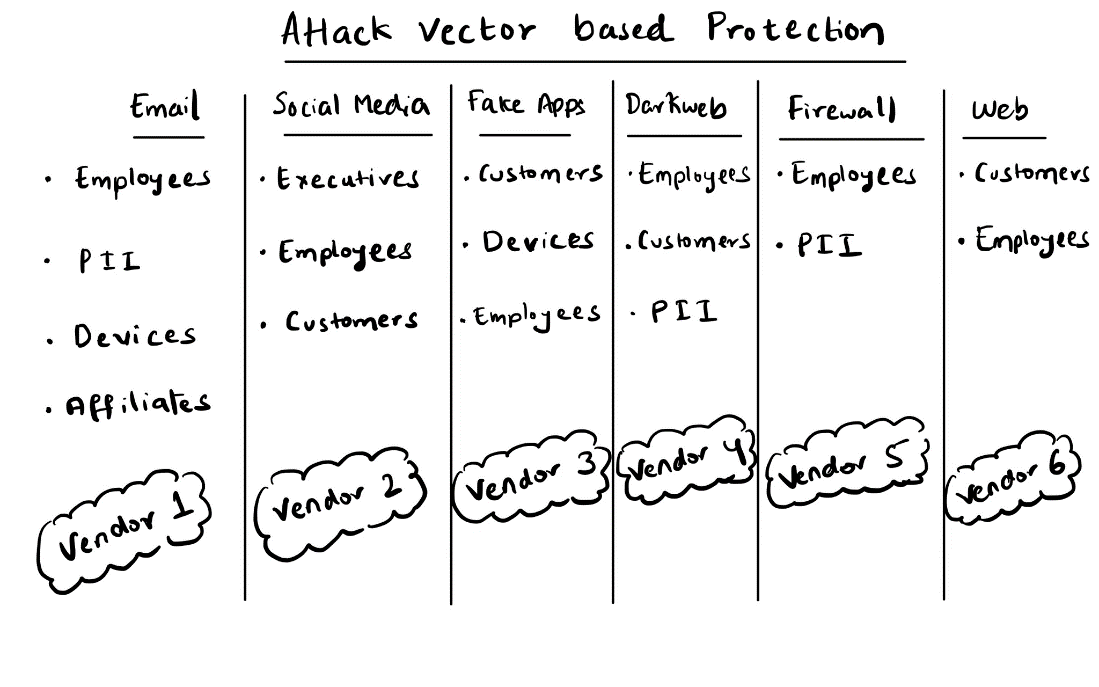
Pitfalls of the traditional Vector-Centric Security
Let's take a closer look at the vector-centric approach. A snapshot of the system looks like the image above. If a brand/ organization wants to protect its employees, it must purchase email protection from a vendor (Vendor 1 in the chart above), social media protection from another (Vendor 2), dark web credential leaks monitoring from a third (Vendor 4), and so on. Then, repeat the cycle for fake apps, phishing URLs, and other attack vectors. This approach creates vendor bloat, making assessing threats across multiple vectors targeted toward your assets impossible.
Try answering a crucial question: What specific and emerging digital threats target your CEO? To comprehensively address this critical issue, there is a need to extract and analyze data from at least four vendors and build dashboards and reports on top of the data. This requires a significant investment of resources, even with assistance from multiple vendors. When we try to answer questions that are much more complex than this, the data collation gets more complicated. No tool can give the external threat posture of an organization’s assets.
And that is why we at Bolster want to change our approach towards external threat protection. What if one tool can inform you of the threats against your executives and protect your employees across multiple attack surfaces?
Welcome to asset-centric protection, where the focus is on protecting an asset, the target, rather than defending against various specific attack vectors, the method or pathway of attack.
Introducing Asset-Centric Security: getting to the core of the problem
The asset-centric approach focuses on protecting an organization's core: its assets. Assets can be an organization’s domains, employees, devices, and more. For instance, to protect an organization’s domain, yourorg.com, a security vendor must monitor and take down typo squat variants, BEC scams, phishing pages, and more digital risks that are infringing on the domain and its trademarks. Moreover, an organization’s security team will also have to monitor the dark web for hacker chatter on possible past or future attacks on their domain. In an asset-based approach, you have one security vendor that can provide comprehensive coverage of all attack vectors that are associated with that particular asset, in this scenario: your corporate domain. The chart below shows how assets can require protection across multiple different attack vectors:
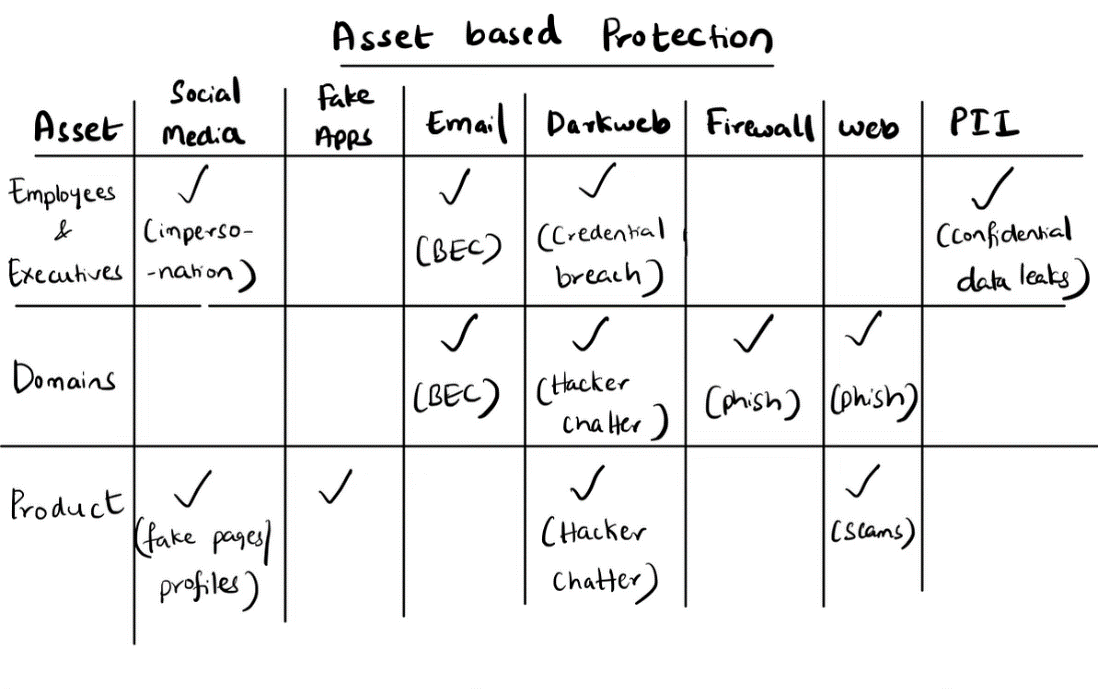
The Asset-based approach is designed to provide a comprehensive level of threat detection, remediation, and correlation across various attack vectors, making it exceptionally powerful when defending against multi-channel l attacks.
For instance, if an executive is being targeted in a BEC attack, the attackers are likely also targeting them on social media and discussing the attack on the dark web. In this scenario, there are multiple attack vectors that indicate a possible attack against an executive. In the traditional vector-centric approach, an organization must purchase two solutions to see the full breadth of the attacker's online activity.
Organizations that approach security with an asset-centric model will see a more accurate risk profile of their aggregated digital risk. Organizations identify their critical assets, such as their executive team, and then generate a risk profile for each asset to understand who on the executive poses the most amount of threat of a security breach to that organization over time. Another significant advantage of asset-centric security is that it eliminates the need to engage multiple security vendors or solutions, saving on administration and costs.
In an asset-centric approach, organizations can streamline their security infrastructure and reduce complexity by relying on a single, integrated solution that addresses all the various threat vectors associated with a particular asset. In doing so, the management and maintenance of security systems are simplified, and the overall security posture is heightened.
Scaling Asset-Centric Security Through LLMs
Large language models (LLMs) play a vital role in scaling an asset-centric security approach because they can effectively organize data, categorize threats, and attribute them to specific assets. Traditional security approaches often struggle to handle the vast amount of data generated on the internet and categorize them accurately. However, with generative AI powered by LLMs, organizations can leverage advanced natural language processing capabilities to extract insights from massive amounts of data to understand the context and threat. The scalability provided by large language models empowers asset-centric security approaches by enabling comprehensive and efficient threat management at scale. scalability provided by large language models empowers asset-centric security approaches by enabling comprehensive and efficient threat management at scale.
Organizations can harness LLMs to gain valuable insights, act, and generate comprehensive reports. How easy would having an LLM summarize the digital threat landscape targeting an organization's CEO be? Furthermore, this approach enables the correlation of the summarized information with global and industry trends, providing a holistic view of the threat landscape. In contrast, such a level of sophistication and comprehensiveness is unattainable with the vector-centric approach due to the complexities of collating the relevant data.
Bolster's unique capabilities to apply large language models across massive datasets gives insights across vectors and provides a comprehensive risk understanding across various assets of an enterprise - employees, domains, and apps. We are working on the next generation of our platform to bring all the intelligence together, focusing more on assets, the target of attack. Asset-centric security will simplify the lives of our customers and their teams by providing both better security and lower friction. It will also provide visibility and easily accessible reporting for analysts who deal with digital threats daily and executives who require a quarterly summary of these threats.






